Claviste FW is using cOS Core OS. Its OS running at the top of linux machine like in checkpoint. It is UTM firewall as it supports features like Routing, FW policies, NAT, ALG (application inspection), VPN, TLS termination, Application control, Anti-Virus scanning, IDS/IPS, Web content filtering, Traffic management (shaping, LB, QoS), HA, Virtualization, etc.
cOS Core Building Blocks
- Interfaces – The following types of interface are supported in cOS Core:
- Physical interfaces – These correspond to the actual physical Ethernet interfaces.
- Sub-interfaces – These include VLAN and PPPoE interfaces.
- Tunnel interfaces – Used for receiving and sending traffic through VPN tunnels.
- Logical objects – Logical objects can be seen as predefined building blocks for use by the rule sets. The address book, for instance, contains named objects representing host and network addresses.
- Rule sets – Finally, rules which are defined by the administrator in the various rule sets are used for actually implementing cOS Core security policies. The most fundamental set of rules are the IP Rules, which are used to define the layer 3 IP filtering policy as well as carrying out address translation and server load balancing.
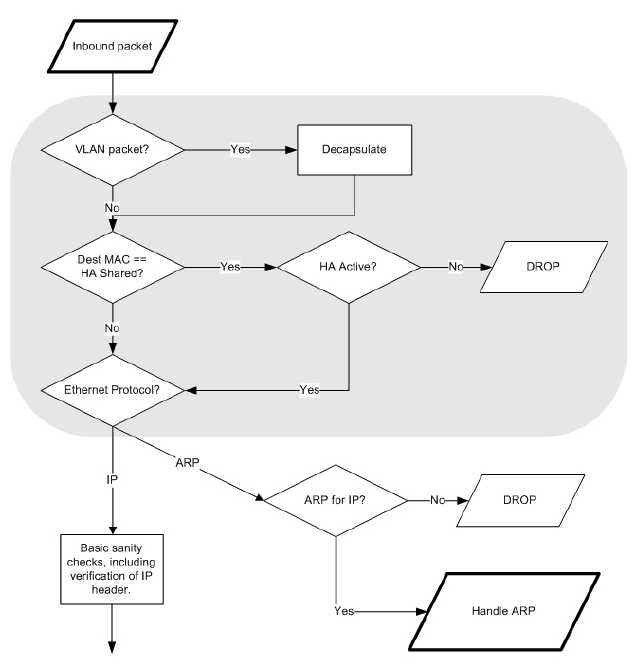
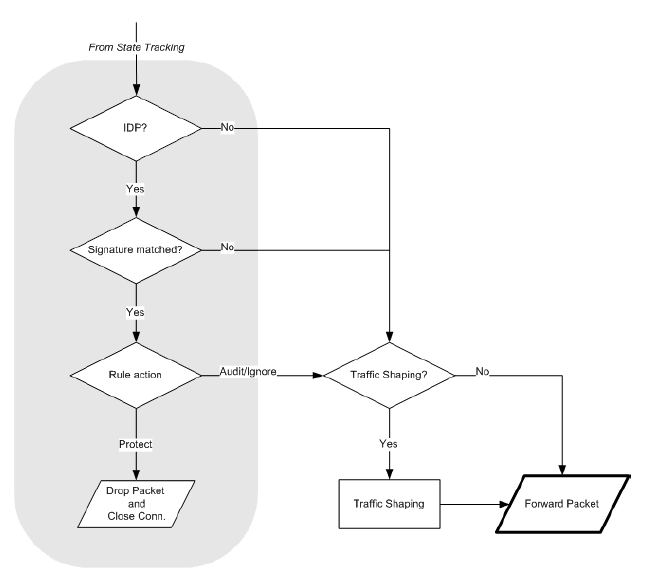
Basic Packet Flow
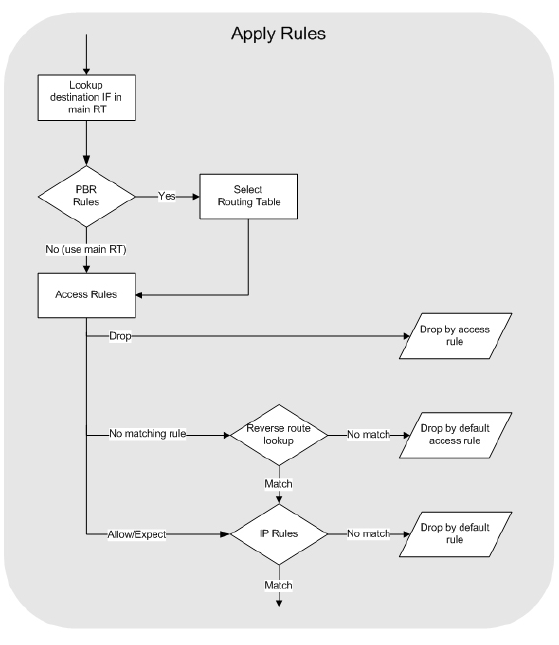
In pictures below you can see the basic packet flow in the clavister FW. What can be unclear is the AllowNAT/SAT vs SAT_ApplyRulePack. Let me expain it. In clavister you can specify rule which will make the connection stateless (FwdFast). In that way the FwdFast/SAT leg in picture is used and connection is not tracked. Also when you check how Apply Rules looks like closer you may see Access Rules and IP Rules. Access rules are for there because of IP Spoofing check. It checks the source network in a packet if its in apply rules and what action should the FW take. If there is no explicit rule, the implicit default rule is taken in which case the reverse route lookup happen. IP rules are then regular ACL.
Apply Rules closer look