Lets say employee wants to break security policy and use ssl tunnel in work to his home or to some vpn service on Internet. And via this encrypted tunnel he can access all he pages and he can do everything like he is indeed home. Checkpoint can do a HTTPS inspection and if employee is violating security policy, hence drop the connection.
The principle is very easy. If Bob tries to create ssl tunnel, checkpoint sees the https traffic and intercept it. Then instead of relaying that connection to destination, checkpoint sends its own certificate and Bobs browser accept it, because it is configured to do so. Then checkpoint creates its own ssl tunnel towards the destination. Hence working like proxy. After that the checkpoint can see what is inside that tunnel and recognize if employee is violating policy. However, you should be damn sure you are not inspecting for example banking transactions. This can be accomplished by using URL filtering as then checkpoint will know all the financial institution around.
This concept can be also used for clients accessing encrypted resources in DMZ for example. And the checkpoint works here like proxy having the certificate of the server. Its like LB ssl offloading. Checkpoint then answer for this request and encrypted tunnel is created between checkpoint and client, so checkpoint can inspect the traffic.
Setup of HTTPS inspection is really straightforward:
- Enable feature on FWs
- Manage Certificates – you should have certification if you want to intercept bobs traffic to outside ssl server
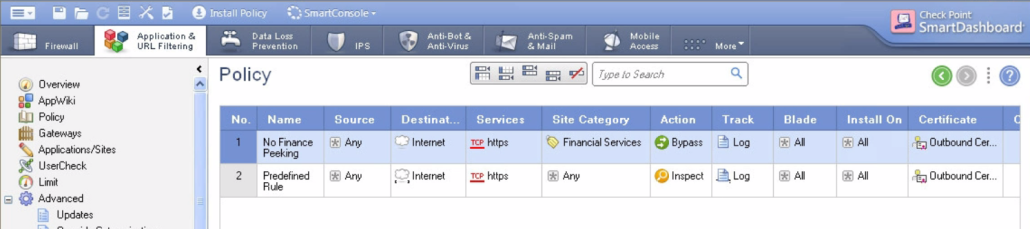
- Configure rules – when we configure the https inspection there is a default rule that shows up for using the https inspection, however we can configure specific rules that would for example disable or bypass https inspection if clients are going to finance institutions or if we want to make other exceptions.
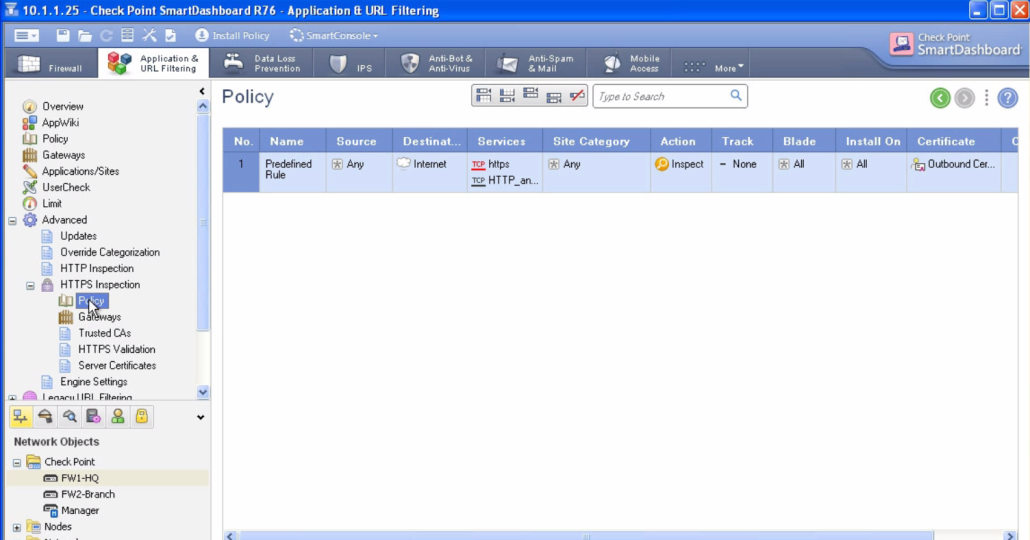
To see the https inspection policy you have to go to App and url filtering and then to advanced – https inspection – policy. As is in the picture below.
The rule you see in the picture above is the default rule when you turn on the https inspection. You can see that source is any, destination Internet, services https and https proxy (8080 by default), Site category is any – that means we are not excluding bank transactions! In the next picture you can see that is very easy to exclude or bypass financial institutions. The db of sites in checkpoint is updated via cloud.