I know how the VPN works. There is IKE phase 1,2. In phase one there is HAGLE going on. In phase two HAGLE but HA is same, becasue (message + password) x hash is used for authentication and integrity check.
Configuration of VPNs under checkpoint is very easy. In checkpoint there is some nomenclatures:
- vpn community – it is the whole VPN topology. VPN networks (VPN domain)+ the VPN gateways (community member). Community can be identified by different topologies like hub and spoke VPN (star) and full mesh.
- community members -VPN gateways
- VPN domains – networks that are encrypted in the tunnel. Same as networks in crypto match acl.
- vpn site – this term is pretty self explanatory. It includes the domain and its community member.
Once we know all this checkpoint vpn terminology we just identify all of it and tie it together. Beware!! Also in checkpoint you have to create NAT exception for VPN if you have most commonly PAT in place for Internet access.
Configuration steps
- Enable VPN feature on Gateway
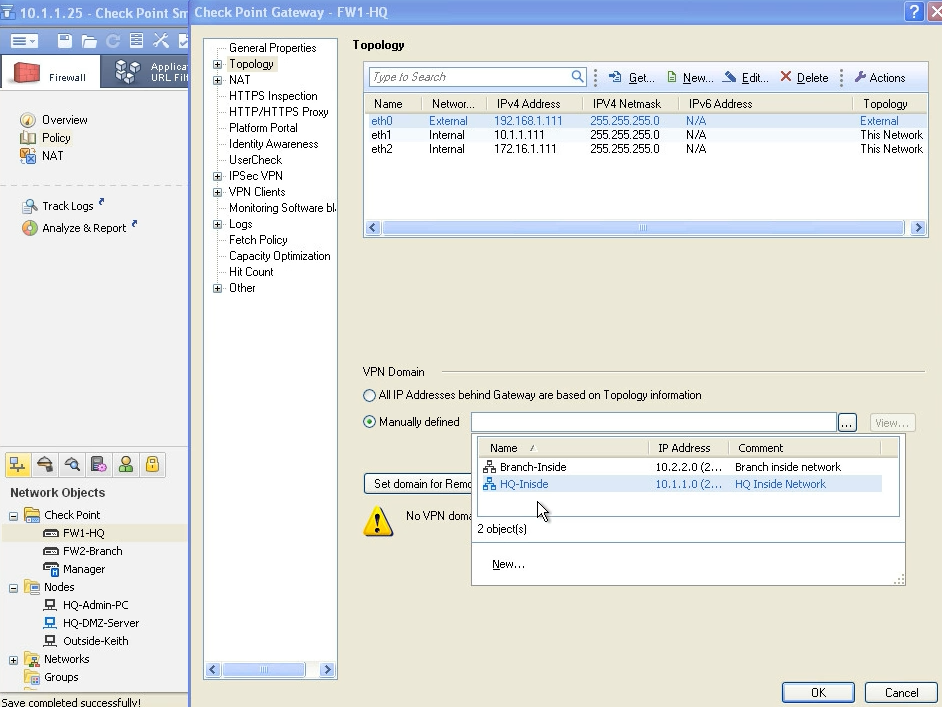
- Identify the VPN domains
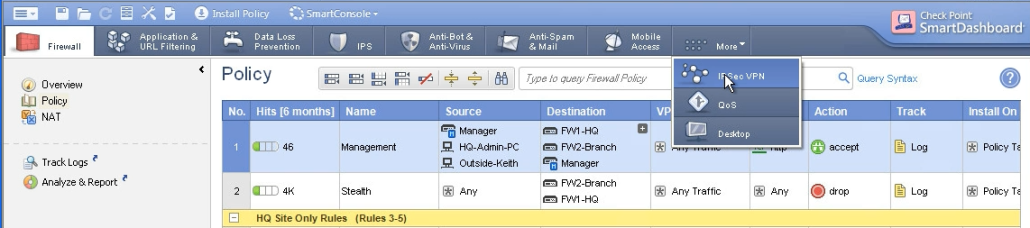
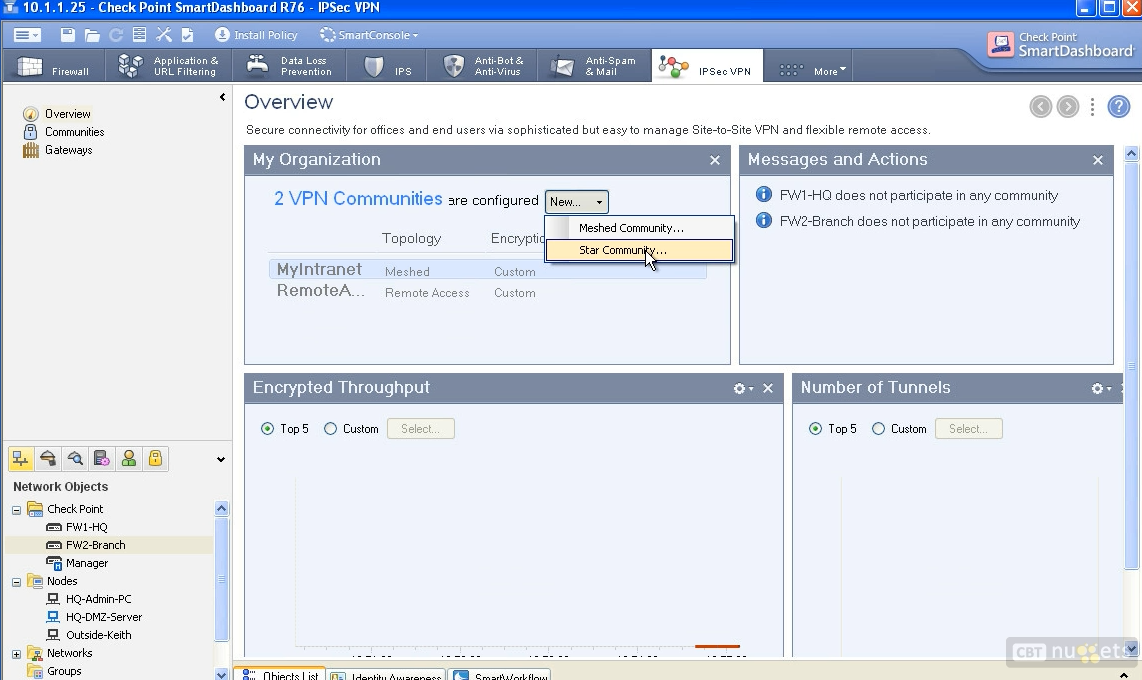
- Create community
- Add rules
In the picture you can see how to identify the VPN domains.
Next step is to configure the VPN community. In the picture you can see how to access it.
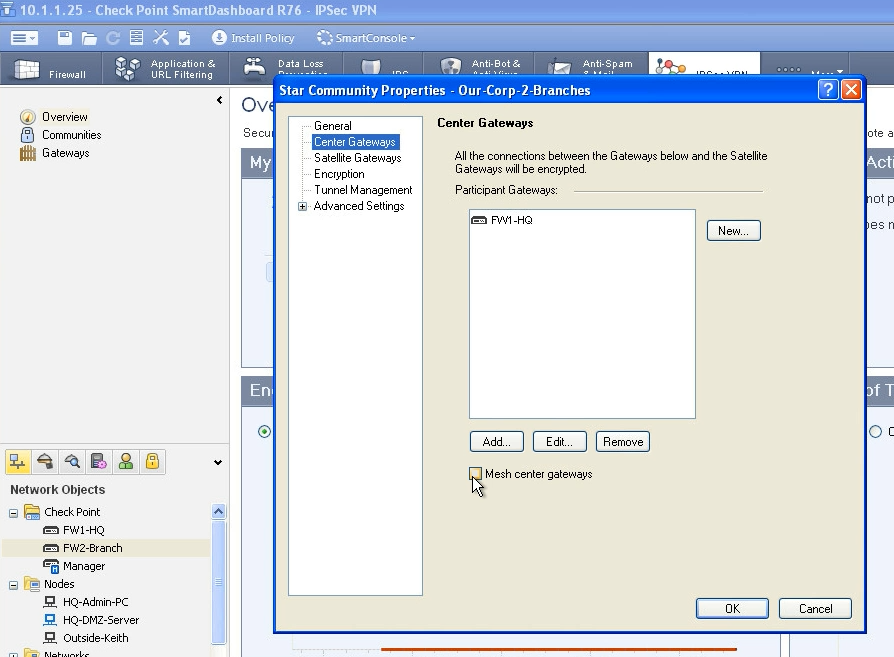
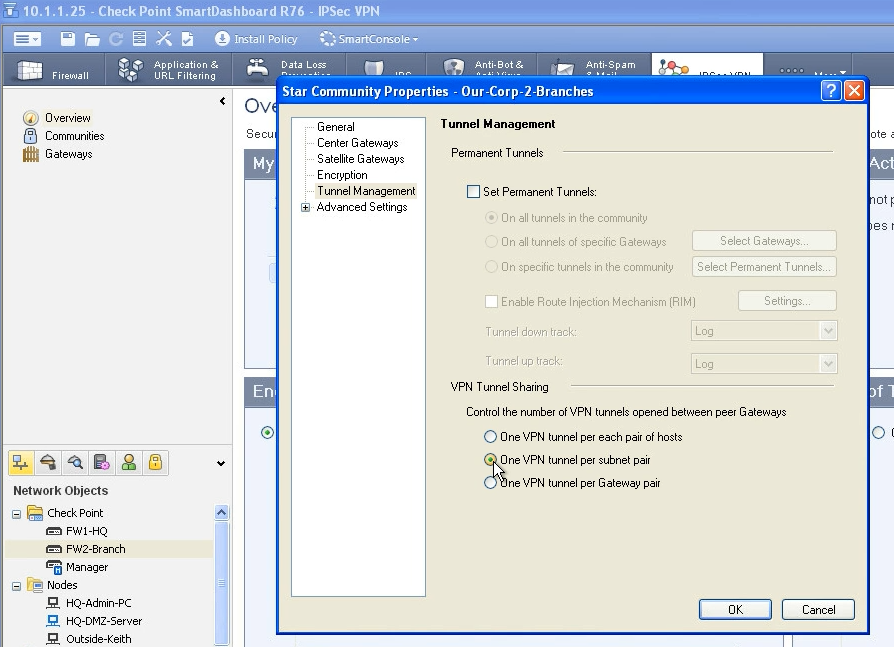
If you put more center gateways (hubs) to your VPN community and mark that „mesh center gateways“ checkbox you create redundant pair of VPN communit members! Nice 😉 Check the screenshot
This is very interesting!! Check the screenshot below. Its regarding how ipsec sa are created. Maybe thats why you have problems on VPNs between Cisco, Checkpoint and other companies.
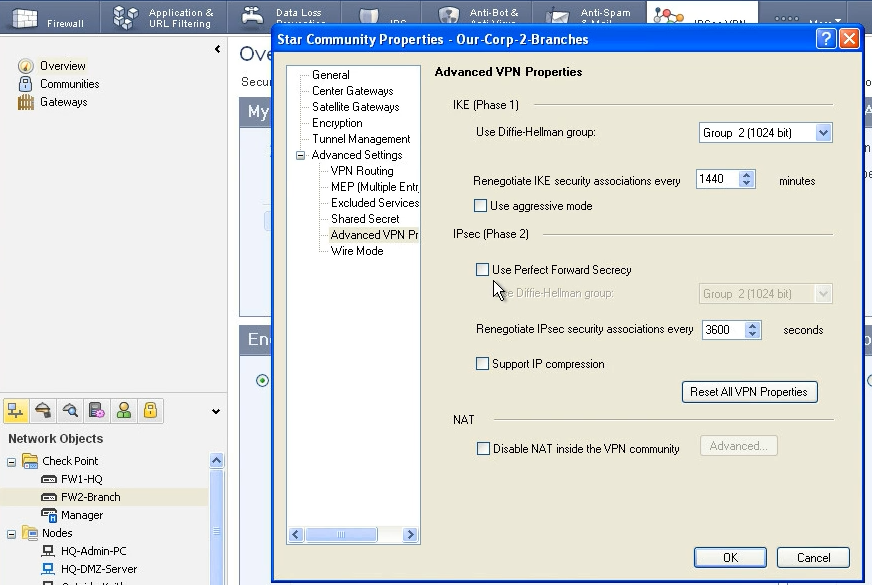
In the next screen you can see configuration for Advanced settings. There you can set up the shared secret for authentication. Also the PFS for phase 2. I strongly recommend to turn on the PFS, because then the IPsec sa would use the IKE sa password for encryption. And you know that the phase 1 tunnel can host many phase 2 tunnels – depends on my setup (crypto map acl and here tunnel management settings), so then every phase 2 tunnel would use the same password! Hacker needs to hack just the phase 1 tunnel. PFS regenerate the encryption password in every IPsec sa tunnel again. But most important you can disable NAT here!!!
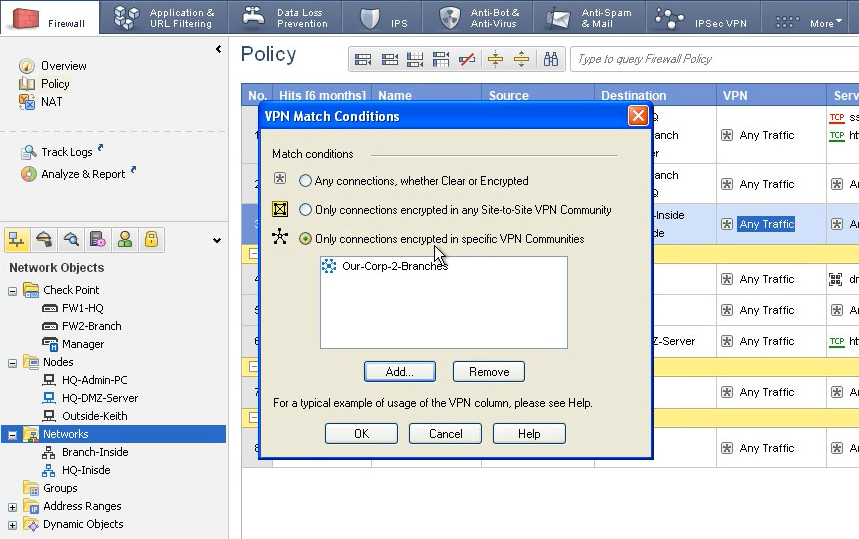
Last step is tu add rules. By this you identify the interesting traffic for VPNs. As you already have configured the communities and domain you just tie that together. You add new rule, put the interesting networks to source destination, and under the VPN filed you put there that VPN community you already created.
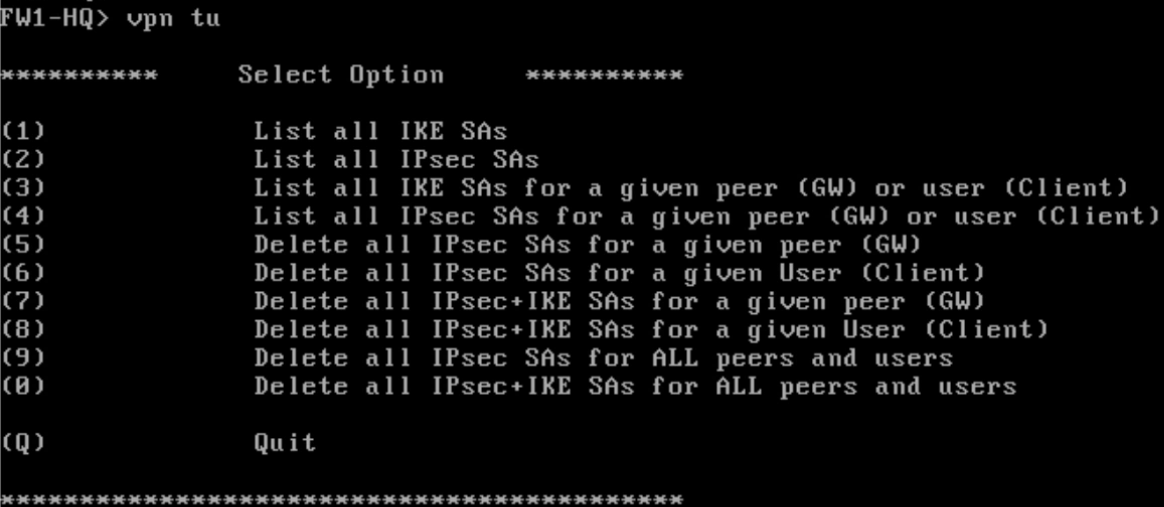
VPN tshooting
In CLI there is very cool tool for VPN tshooting. Its called vpn tunnel haha 😀 yeah I am not kidding check the screen to see more of it.