If we ask someone with some technical background what breaking ciphers is about, he/she will most likely say that code breaking has to do with heavy mathematics, smart people and large computers. We have images in mind of the British code breakers during World War II, attacking the German Enigma cipher with extremely smart mathematicians (the famous computer scientist Alan Turing headed the efforts) and room-sized electro-mechanical computers. However, in practice there are also other methods of code breaking. Let’s look at different ways of breaking cryptosystems in the real world.
Classical Cryptanalysis
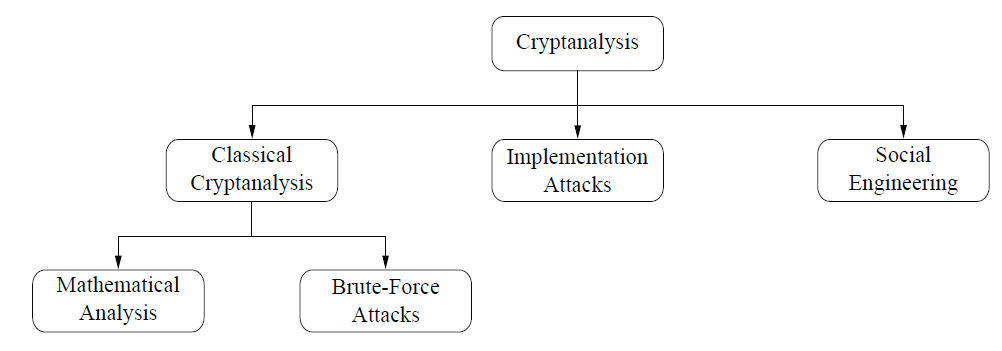
Classical cryptanalysis is understood as the science of recovering the plaintext x from the ciphertext y, or, alternatively, recovering the key k from the ciphertext y.
Cryptanalysis can be divided into analytical attacks, which exploit the internal structure of the encryption method, and brute-force attacks, which treat the encryption algorithm as a black box and test all possible keys.
Implementation Attacks
Side-channel analysis can be used to obtain a secret key, for instance, by measuring the electrical power consumption of a processor which operates on the secret key. The power trace can then be used to recover the key by applying signal processing techniques. In addition to power consumption, electromagnetic radiation or the runtime behavior of algorithms can give information about the secret key and are, thus, useful side channels. Note also that implementation attacks are mostly relevant against cryptosystems to which an attacker has physical access, such as smart cards. In most Internet-based attacks against remote systems, implementation attacks are usually not a concern.
Social Engineering Attacks
Bribing, blackmailing, tricking or classical espionage can be used to obtain a secret key by involving humans. For instance, forcing someone to reveal his/her secret key, e.g., by holding a gun to his/her head can be quite successful. Another, less violent, attack is to call people whom we want to attack on the phone, and say: “This is the IT department of your company. For important software updates we need your password”. It is always surprising how many people are naive enough to actually give out their passwords in such situations. This list of attacks against cryptographic system is certainly not exhaustive. For instance, buffer overflow attacks or malware can also reveal secret keys in software systems. You might think that many of these attacks, especially social engineering and implementation attacks, are “unfair,” but there is little fairness in real-world cryptography. If people want to break your IT system, they are already breaking the
rules and are, thus, unfair.
Solid cryptosystems should adhere to Kerckhoffs’ Principle, postulated by Auguste Kerckhoffs in 1883:
A cryptosystem should be secure even if the attacker (Oscar) knows all details about the system, with the exception of the secret key. In particular, the system should be secure when the attacker knows the encryption and decryption algorithms.
Important Remark: Kerckhoffs’ Principle is counterintuitive! It is extremely tempting to design a system which appears to be more secure because we keep the details hidden. This is called security by obscurity. However, experience and military history has shown time and again that such systems are almost always weak, and they are very often broken easily as soon as the secret design has been reverse-engineered or leaked out through other means. An example is the Content Scrambling System (CSS) for DVD content protection, which was broken easily once it was reverseengineered. This is why a cryptographic scheme must remain secure even if its description becomes available to an attacker.