How do we acquire the actual identity of users in your network? How do we acomplish that firewall will know the users and can map them to theirs specific IP address. Here are the possibilities:
AD Query – when user logged into the AD the Security Event Logs triggers including also IP address info about user. So if FW is communicating with the AD and is aware of Security Event Logs, it can see based on IP address who the user is. Then in the FW logs you can see source, destination, service, username.
Captive Portal – the AD Query is nice but what if someone is using the Tablet or smartphone to access Internet through our FW. How can FW know who the user is? The answer is Captive Portal. If the FW doesnt have the asssociation IP-Username then it intercept the user session and ask via captive portal for the credentials. If user is using http the captive portal changes to https for secure login. The captive portal can authenticate users locally or via AD, etc… it depends on your configuration.
Agents – you can you software agent which has to be installed on users PC to authenticate itself. For example endpoint or citrix terminal services
VPN – also VPN is one of the options for users to authenticate themselves from outside. Once authenticated we can use that info and bind user to its IP address
There are 3 steps to turn on identity awareness feature:
- enable feature
- create access roles object – object have to contain ip address, and user has to be member of LDAP group, local db or some other db
- use the access roles in rules – use the created access role object in your rule. For example source is your access role object, destination is your internal network, service HTTPS, action PERMIT
In the picture you can see how you enable the identity awareness feature along with the AD/Captive Portal/Agents
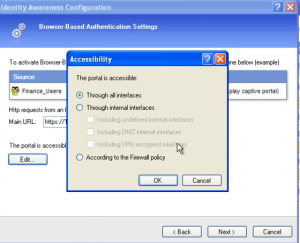
When you click next you can configure your AD and try to connect if its successful. Then the next thing is configuration of the Captive Portal itself. As in the screen you can see that by default it is set up for internal IP address and internal interface. You have to edit that! How checkpoint identify what interface is external? By default where the default root points that is the external interface!!!!
When you click edit, you will see the configuration below. When you select all interfaces it doesnt mean that the portal will prompt for credentials for all the traffic through all interfaces, it just turn on feature on all interfaces and you can put a rule to the policy so the rule will match all the interfaces.
You can create access roles by going to users and administrators tab and then right clicking on access roles – create new access role
When your access role is created you can use it in the access rule. In the picture you can see also that you need to edit accept action to enable captive portal. This enables to redirect the traffic to captive portal If traffic come with unmaped user (ip to username).