General overview of checkpoint rules are:
- Mgmt rules – needed for the access of physical server. You should allow also ssh and https for specified client because you may have problems with SIC so you want to connect directly to FW
- Stealth rules – you dont want any external user connect to the FW, you should configure the rules to drop and log the all traffic trying to reach the FW and to see who is trying
- Internal rules – internal clients are in most cases allowed to reach lots of resources. You have to specify it because there is implicit deny rule at the end
- Cleanup rules – although at the end is implicit deny rule, specify explicitly deny rule so you can log this rule and see who is trying to access what and is unsuccessful. This rule helps a lot during tshoot to see in smartlog if the connection is closed in FW for complaining user.
- Tweak „implied“ rules – checkpoint implements some implicit rules for example to drop icmp, etc… You can remove them or edit them and decide where you want to place them (Top or Bottom of ACL). We can also tell the fw to do the logging on these applied rules when tshoot.
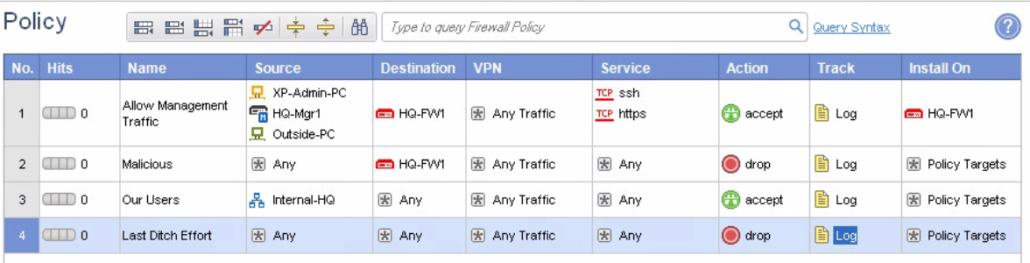
In the picture you can see how the rules looks like in checkpoint. The adding rules is not any rocket science. You just click and add, you can drag and drop the objects or add them via the plus button in every row. There is also column named install ON. Here you can choose to which FW you would like to install the policy otherwise it is intalled on all the FW and I think you dont want that. Dont forget to save the rules and then push them to FW.
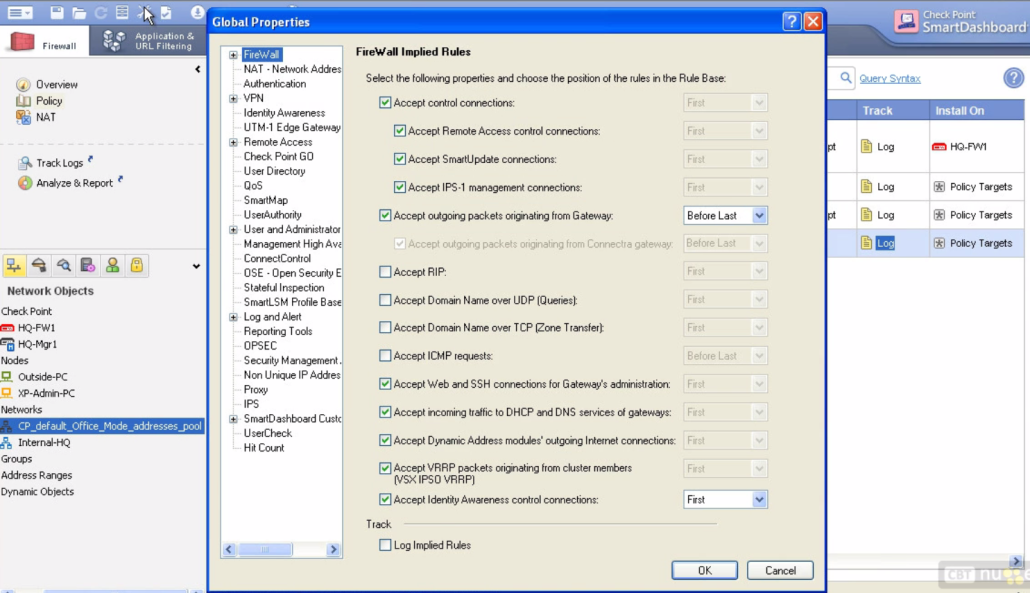
If you want to see the implied policies you should go to File – Policy – Global Properties or just click on edit the global properties button from the top icon bar. Check the picture below. The control connections are needed for mgmt server to manage the fw. The accept outgoint packets originating from Gateway is for FW to be able to ping someone or create a connection to some resources outbound. Check the placement before last 😉 The recommended is to check the log the implied rules.
To see the implied rules you have to go to File – View – Implied rules. There are maaaany of them applied. Most are first and some before last.
Policy mgmt via CLI
By default checkpoint FW implements a default policy and restrict for example ping to its IP address. If you pushed some policy and you are now not able to connect to FW or you are not able to manage the FW via mgmt server you have to console it and access the CLI. Then you update the policy in mgmt server and fetch it via cli in the physical FW.
The basic commands are:
- fw stat – to see the last policy installed, by which host, on what date and what interfaces
- show route – to see the routing table
- show configuration – to see config
- show configuration interface – to see more granular configuration
- fw unloadlocal – by this command you unload the policy from localhost
- fw fetch local – by this command you fetch the policy from localhost. You can also do it from mgmt server by typing instead local the ip address
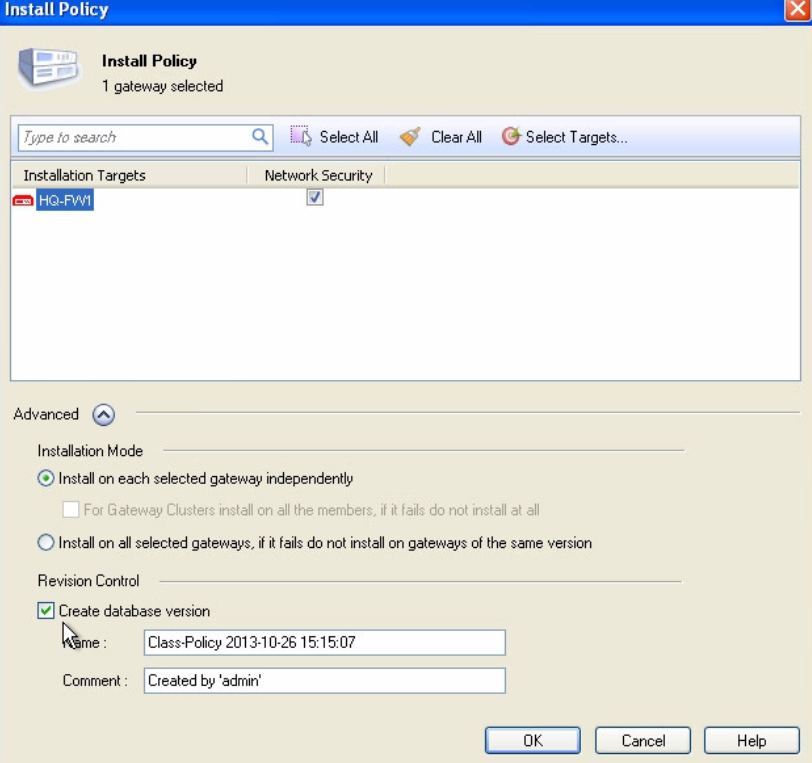
When you installing the policy you can go to advanced and create a snapshot of whole database. It is the create database version checkbox. Then you just click OK to install the policy and you can see the actual status. Below in the main screen is the link for Policy installation status where you can see what was installed and when.